In yet another crackdown on the Google Play Store, Google has removed hundreds of phony and terms of service breaking applications (apps). The Play Store is the official app store for the Android Operating System (OS). In a survey conducted by software company Lefttronic, it is estimated that Android is the most dominant OS with 76% of the market share. Moreover, Lefttronic’s forecast suggests this number will only jump to 87% by 2022. This means every business currently has or will have at least one Android user and with many small and medium sized businesses (SMBs) permitting Bring Your Own Devices (BYOD), employees utilizing Android OS pose a major security risk.
Leveraging the Play Store for malicious objectives
For years, hackers have been using the Play Store to distribute backdoors, malware, and spyware, capable of stealing a range of data. While Google has an app vetting process, we are seeing cybercriminals use numerous techniques to circumvent the security verifications. Android OS in comparison to Apple iOS, can run on different hardware and manufacture platforms, meaning there is no centralized patch management or update system for each device. Instead, each manufacture is required to push updates and security patches for their devices, and unfortunately “sell and forget” is a common methodology. It certainly doesn’t help that every newly downloaded app is accompanied by a host of risks and beyond storage issues, individuals rarely see the risks in filling up their phone with apps.
 |
|
|
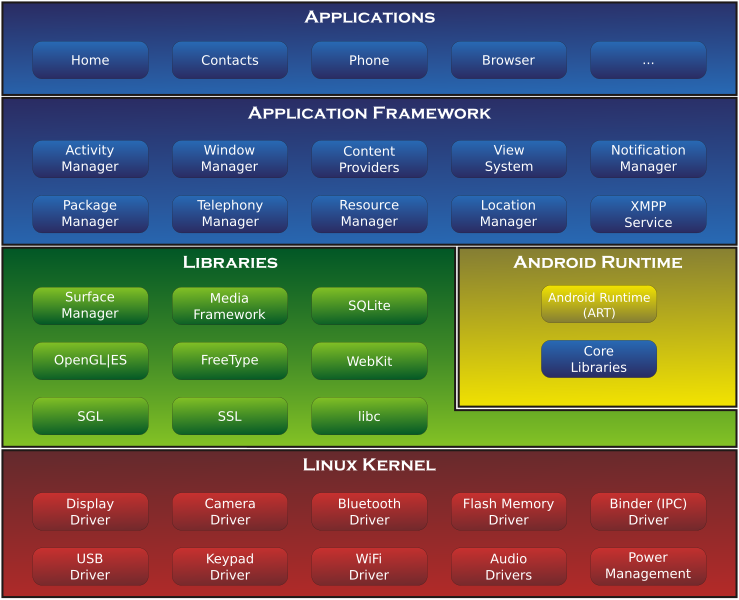
Google Play Store |
iOS App Store |
|
Apps require lots of permissions to run because OS is open source, but more flexibility and control over app behavior |
Tightly controlled apps running on proprietary file system, but more mobile device security
|
|
|
 |
In one campaign, hackers initially submitted a benign version of their app and later added a backdoor after it was accepted. In another, the adversaries asked for little permissions during installation, then later requested them using hidden code in an executable file. These campaigns are successful with time as the apps provided backdoors that could report information about the infected phone's hardware, android version, and installed apps. This information could then be leveraged to download and execute malicious payloads specific to a device, reducing the time it generally takes to discover and exploit vulnerabilities. While payloads that aim to collect call logs and contacts are not too dangerous, others enable cybercriminals to steal SMS messages, location details, and credit card data.
Remote Code Execution via Android OS
The most common method to spread malware is through apps. Furthermore, for “fear of missing out” users are often quick to download apps with millions of downloads without verifying them. Android devices are more prone to infection because they are open source and subsequently more likely to have vulnerabilities because their code, unlike proprietary, is not worked on for months before it is released to production. Using a device that already has OS vulnerabilities opens a door for hackers to exploit and unfortunately, devices running Android OS are disproportionally plagued by this. Just this week an Android Security bulletin revealed that at least 36 vulnerabilities were discovered within the Google Android OS. While not all have severe levels of impact, some could allow for remote code execution within the context of a privileged process.
In Android vernacular, a privileged process is a trusted app with privileges a third-party app cannot obtain. Depending on the privileges of an app, an attacker could potentially install programs, view, change, or delete data upon exploiting the vulnerability. They could also create a new account with full user rights, further allowing for more remote code execution, information disclosure, and privilege escalation to name just a few repercussions.
Latest Play Store campaign, a secret network of app developers
In this year’s latest report from CyberNews, a privacy focused research company, researchers discovered 103 apps with more than 69 million installs to be linked to a secret network of organized developers in China. The researchers established that numerous seemingly unconnected apps have too many commonalities to be a coincidence. For one, all of the discovered apps were published by a handful of developers with western names like “Alex Joe.” They then have identical privacy policies, Gmail addresses, and holding pages which are shortened with a bit.ly link. Being that there are so many apps, researchers are leaning towards an automated cloning process. The apps gained major popularity because they were Trojan clones of popular apps like photo editors and makeup cameras.
Repackaging legitimate apps in the Play Store is a tactic that has been used for several years and is why more malware is likely to target devices running Android OS. In this particular campaign, the developers abuse permissions to achieve their goals. While a camera app clearly needs access to a device’s camera, does it also need to view the network connections and emails? Herein lies the issue that is not the suspicious developers, but the amount of dangerous permissions found in the apps.
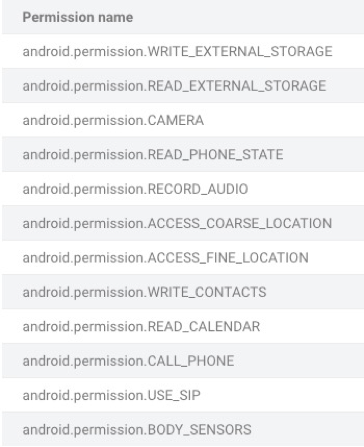
For instance, a calculator app has no valid reason to request for location, contacts, or read and write permissions. Users accepting these types of permissions are allowing the app to scan all of their files – including images, documents, and anything else saved on their device. The image below is CyberNews analysis of the most requested permissions from the phony apps.
Image via CyberNews
Why do they do it?
The motive behind scammy apps is usually to make money, but how do free apps make money? The answer is often through selling collected data to marketing agencies. As once a large user base is established, companies can quickly leverage it for advertising. Putting the recent Play Store campaign aside, it is believed that 7 out of 10 free apps have embedded commercials to generate revenue per banner display, click, and install.
Numbers estimate that $0.10 is giver per banner ad click and $5 per video ad shown. Running some simple calculations if 1 video ad were to be shown a day on the perceived 69 million installs, the adversaries would get 6.9 million dollars from banner ads alone and the more apps pushed out the more revenue. Of course, not all the apps are being used on a daily basis or kept on a phone, but that still is a massive amount of revenue for little work.
SMB’s overlooking BYOD threats
Employers and small business owners with tighter budgets commonly see no danger to their business in personnel using mobile devices for work. However, the risk of data theft or loss of a device could cause serious damage to a company because unlike workstations, mobile devices rarely have endpoint protections like antivirus, firewalls, and encryption. It is important to note that most businesses are interested in securing mobile devices, but that a.) they believe security tools offered in free solutions are sufficient and b.) that there is no added value in spending money on dedicated solutions.
This attitude is one in which employers and device owners employ. It can additionally be exploited by cybercriminals. The usefulness mobile devices provide would make it silly to ban them, however, their mobility is a double-edged sword. They enable employees to do business tasks anywhere, but they can simultaneously be lost anywhere. The loss of sensitive data via a personal device is a common occurrence and one reason organizations should consider a dedicated mobile device management solution that addresses modern trends and security requirements.
Despite Google taking a very active role in policing the Play Store, its app bans come off as a reactive rather than proactive solution. Unfortunately, users are increasingly downloading presumably safe productivity apps, and unknowingly opening up their personal and company data to abuse. At the end of the day, free apps are free for a reason and just because an app is on the Play Store, does not mean it is automatically safe to use.
What is your organization’s mobile device policy or contingency plan for Android devices? If you need support defining security and organizational governance for mobile and personally owned devices, contact us for a complementary consultation.