The Cybersecurity Maturity Model Certification (CMMC) is a third-party assessment program created by the DoD to gauge the maturity of an organization's cybersecurity practices and verify the protection of Federal Contract Information (FCI) as well as Controlled Unclassified Information (CUI). When CMMC 1.0 was released in 2017, there were concerns amongst government contractors as it was incredibly pricey for small organizations, contained vague language of CMMC assessment process, and did not include a lot of overlap in cybersecurity requirements to other federal requirements or commonly accepted standards.
The Department of Defense recently revamped CMMC after reviewing vendor complaints concerning the cost and complexity of CMMC. We have compiled a brief yet informative graphic of the new level requirements.
Elimination of Levels 2 and 4
CMMC 1.0 was made up of 5 levels. That being said, Levels 2 and 4 were CMMC exclusive practices that did not align with widely respected organizations like NIST. Furthermore, Levels 1 and 2 were effectively useless as level 3 and above was required to handle CUI. The DoD arrived at a solution that solved both these areas by removing Levels 2 and 4 in CMMC 2.0, leaving only 3 levels. Having only 3 levels streamlines the CMMC model by focusing on the most critical security controls.
| Level 1 Basic Cyber Hygiene |
Safeguard using universally accepted cyber guidelines |
| Level 2 Intermediate Cyber Controls |
Transition into cyber maturity to protect CUI |
| Level 3 Adequate Cyber Controls |
Protect CUI data, includes coverage of all NIST SP 800-171 controls |
| Level 4 Proactive Cyber controls |
Provide sophisticated security practices |
| Level 5 Advanced Practices |
Protect CUI and reduce the likelihood of Advanced Persistent Threats |
Level 1 is still the same at basic cyber hygiene and is all most organizations who are not handling CUI will ever need. This is most beneficial for contractors solely handing FCI. Level 2 was previously 3 and is based on criticality. For example, if you have CUI related to national security you will be assessed by a 3rd party on a much more rigorous frequency. CMMC 1.0 required a 3rd party assessment every 3 years and CMMC 2.0 requires an assessment 3 times a year. Unfortunately, what constitutes criticality is yet to be decided in the DoD rule making process.
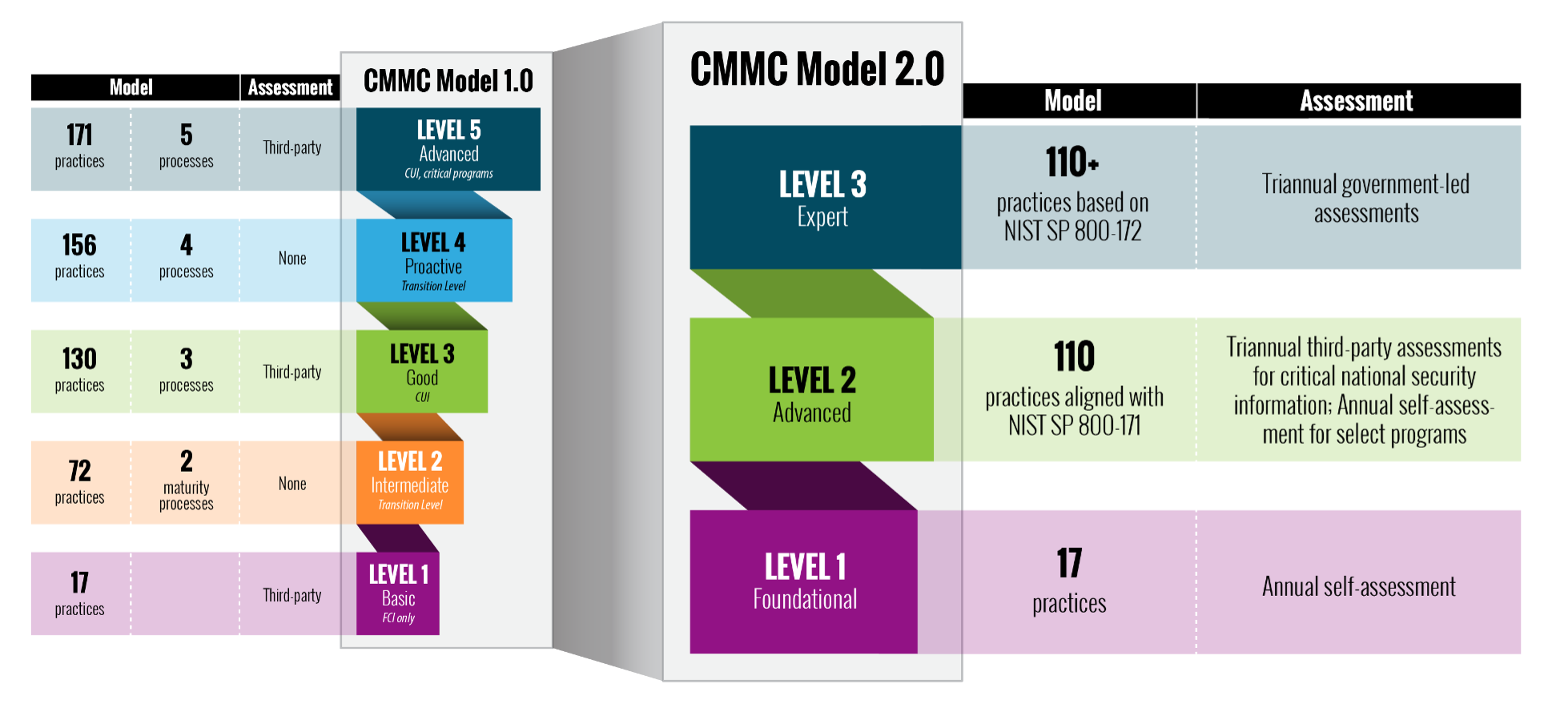
Graphic courtesy of https://www.acq.osd.mil/cmmc/
Level 1 Self-Assessments instead of 3rd Party Attestation
One of the largest noticeable changes to CMMC 2.0 was how Level 1 certifications were reached. Level 1, basic cyber hygiene has been modified to require DoD contractors to implement NIST SP 800-171 and its 17 controls. Level 1, conversely, maybe self-attested for. The idea being contractors will upload a yearly self-assessment report to the DoD via the Supplier Performance Risk System (SPRS). This saves capital from needing to pay for an assessment. Nevertheless, SPRS requires knowing how to assess and calculate existing controls.
The DoD has stated the changes to implement in CMMC 2.0 will be implemented through the rulemaking process, which the DoD anticipates being anywhere from 9 months to 24 months.
All in all, the model has not drastically changed nor have its expenses. The controls are mostly the same but the timeline to implement them has sped up as well as the number of times contractors will be assessed.
Is your organization ready to commit to building a formalized cybersecurity program aligned with CMMC? Or maybe you are not sure what direction to take? Call Silent Sector today to speak with one of our security experts. We'll give you clarity and help your business get to its desired level of security so you can focus on your core objectives instead of worrying about compliance.


