Last week the FBI’s charlotte office warned social media users to pay close attention to the information they share online and “carefully consider the possible negative impact of sharing too much personal information online.” This alert comes at a time when many people are confined to their homes and consequently taken up social media to pass time during the period of social isolation.
The Double-Edged Sword of Social Media
For most, social media is used to stay in touch with friends and family. Just like in real life, people enjoy sharing things about themselves. This can range from the name of their dog, first grade teacher, and mother’s maiden name. Platforms like Facebook have numerous games and trivia challenges that encourage people to share information about themselves. In which case publicly answering these questions can allow attackers to specially craft a social engineering attack. Social engineering is the formalized process of manipulating others into giving up something. It also happens to be the most effective routes to steal confidential data. Moreover, the majority of data breaches are due to human error from social engineering and not a sophisticated technical heist.
With quarantine cancelling ceremonies, many graduates are posting photos that they are virtually graduating. There is also a high school support photo trend going viral that encourages users to share their high school graduation photos to support the class of 2020. Unfortunately, from scrolling through social media and clicking on a single senior portrait, a scammer can deduce the name of one’s major, school, and graduation year. All three of these are linked to common password retrieval security questions intended to secure or authenticate a user. Moreover, college graduates are naturally keen on announcing where they will be employed. They do this by hash tagging “internship” or updating their social media biographies. This in particular is scary from the employer's perspective because new hires are unaware of the corporates structure or who their coworkers are and thus, make perfect targets for phishing attempts. From platforms like LinkedIn, an adversary can map out the internal corporate ladder and easily identify an organization’s newer employees.
Consider how simple it is to send a fictitious email impersonating a manger and requesting sensitive I-9 documents of a new HR specialist solely based on knowing their supervisor and that they are new to the company. While this scenario sounds ridiculous, it works and has worked perfectly. For one, as a new hire, you are in no position to question your manager. Additionally, scammers are increasingly designing phony emails to appear completely legitimate. It is also worth noting that by no wrongdoing of their own, new personnel are often naïve to help and thus more prone to fall for a phony call from IT security. A phrase like “we just detected something weird on your account – what’s your username and password for us to check” would be enough for many to give up their credentials.
Weaponizing Human Predictability
Human predictability might be seen as a flaw when it comes to password selection because people pick passwords that are easy to remember. Moreover, research indicates that humans tend to show a pattern when making passwords by adding their birthdate, pet’s name, etc. Attackers and scammers leverage this weakness by using password generators like Common User Password Profiler (CUPP). CUPP is an open-source tool that can create custom brute force password dictionaries based on inputted information like a target’s favorite sports team, food, or family member's name. The below graphic demonstrates how easy it is to scrape social media and social engineer potential passwords.
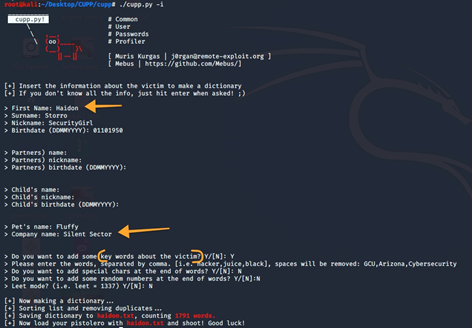
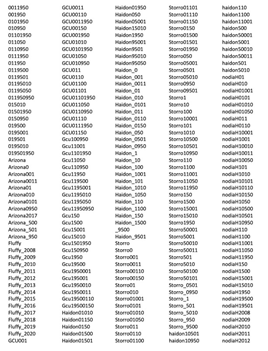
Creating our own password list using CUPP –
1791 results possibilities using full name, birthday, pet and company name
How to be safe, secure, yet still social?
When some post a photo or update they are unknowingly positioning themselves as targets for scams. However, familiarizing oneself with how social media platforms operate can enable people to achieve maximum privacy. Facebook, for instance, has a privacy option to show “Friends Only” updates and posts. While Instagram gives user’s the ability to disable “similar account suggestions” which can prevent other people they have mutual connections with from seeing their account. For the even more security cautious, removing contacts and using an anonymous email can prevent one from being stalked. As sharing personal information like a phone number frequently arises for a number of reasons.
Unfortunately, giving out personal information can be the key for strangers to find all of your social media accounts. Another concern with social media is the proliferation of location-based services. As numerous services today take advantage of mobile device location tracking to offer recommendations. Sharing location and posting updates or photos indicating where one is at can enable a burglar or stalker to target someone while they are away from home or the office.
Despite the benign intention, social media has also led to a noticeable increase in online stalking and cyberbullying. Moreover, it has become addictive to the point many struggle with putting their phones down. This can be contributed to the irresistible temptation in seeing how many likes a photo got or getting a new friend request notification. With these priorities in mind, working and being productive are becoming less relevant. What’s more, is that the younger populace moving into the workforce are particularly more prone to becoming addicted to social media. They are in a phase of life where social interactions play a major role in self-esteem and character development. Nevertheless, by uploading photos that anyone can see, they are making it much easier for stalkers and scammers to get ammo. Cybercriminals are notorious for also catfishing and spoofing legitimate connections to build trust. They then exploit the trust by manipulating one into giving them money or revealing sensitive work information. Just like in the physical world, exercising “stranger danger” is still applicable and one should never accept friend requests or messages from people they do not know.
In all its abundance, social media is not all evil and because it is not going anywhere soon and with the FBI encouraging people to consider the ramifications of oversharing personal information online, it is clear that security awareness training needs to happen sooner rather than later. Research shows that training helps individuals be more prudent about what they share online and how to be more vigilant against social engineering attacks like phishing. At the end of the day, the less personal data shared online and publicly accessible, the better.
Interested in learning what an effective a social media training program will do for your employees? Call us today to hear how we mix training, tools, and relevant content to empower your employees to combat evolving cybercriminals thereby protecting the security of your employees, data, and company.


