In a market where security and IT vendors are heavily saturated it is increasingly becoming difficult to determine which vendors truly have sound security solutions. Moreover, from the vendor perspective, how can they distinguish themselves from their competition? One approach both parties can take is following the risk based approach to cybersecurity recommended by the National Institute of Standards and Technology Cybersecurity Framework (NIST) 8170.
NIST 8170 is the first of its kind in that it encourages organizations to undertake a more analytical risk management strategy. The idea being that this strategy can empower organizations to select specific controls for their needs and industry requirements rather than just check a box for compliance; essentially neglecting security. This, in turn, can reduce the daunting vendor, product, and services pool, essentially helping organizations get the most out of their IT-related and cyber risk investments. The purpose of this document is to uncover how adopting NIST 8170 can help organizations improve their existing security posture and cyber risk management programs.
Not your Typical Framework
Information security frameworks exist to help instill confidence in an organization and establish a reputation for how an organization protects its data and services from danger.
Frameworks act as security blueprints and often encompass policies, security training, and technological controls. NIST released NIST 8170 in an effort to help federal agencies apply frameworks to their existing cyber risk management programs. NIST 8170 exposes the value of cybersecurity frameworks and goes a step further by describing how they can be applied. More specifically it focuses on how organizations can create profiles when introducing new vendors, products, and services to their environment as to not introduce senseless technical risks. The framework was created with federal agencies in mind but can be applied to the private sector as it aligns with NIST's already popular suite of security and privacy risk management standards and guidelines.
NIST 8170 is different from other frameworks because it highlights examples of how to implement the Framework for Improving Critical Infrastructure Cybersecurity (commonly known as the Cybersecurity Framework or CSF) rather than just give organizations a checklist of items to execute. CSF is a completely optional risk-based approach that private-sector owners of critical infrastructure across the U.S utilize. It was published following Executive Order 13636 and 13800 which aims to increase the security of critical infrastructure and reduce national cybersecurity risk through mandating federal agencies use the CSF outline. The CSF views individual cybersecurity risk programs as “profiles,” in which each risk management process should combine business and cybersecurity achievement to manage vulnerabilities and threats associated with the technical environment. This should occur all while factoring in mission goals.
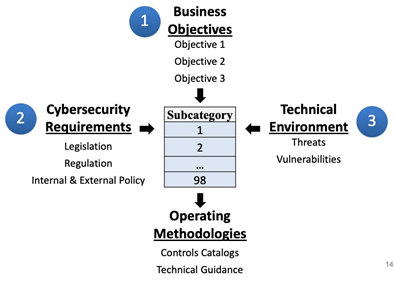
CSF Outlines how a cybersecurity risk profile can be created from three types of information
Graphic courtesy of NIST
Despite these executive orders being passed nearly 3 years ago, many public and private organizations are struggling with implementation. One of the challenges being that CSF lacks precise measurements for how to improve and apply security. This is where NIST 8170 shines. It leverages the CSF document to address common security-related concerns and then insinuates how to map them with controls. This enables organizations to discuss cyber risk management at the technical and business level, allowing them to effectively improve their security capability and cybersecurity risk management.
NIST 8170 breaks down CSF and the ever-growing list of security responsibilities into eight check boxes. Per NIST 8170, NIST believes these eight approaches and concepts support a mature cyber risk management program:
- Integrate enterprise and cybersecurity risk management
- Manage cybersecurity requirements
- Integrate and align cybersecurity and acquisition processes
- Evaluate organizational cybersecurity
- Manage the cybersecurity program
- Maintain a comprehensive understanding of cybersecurity risk
- Report cybersecurity risks
- Inform the tailoring process
Line item 1, “Integrate enterprise and cybersecurity risk management,” is a prime example of how organizations can integrate CSF throughout normal operations like product procurement. For instance, per NIST 8170, when a new solution is introduced it must be viewed from the mission and security perspectives. This inadvertently supports the mission goals, improves cyber risk management, and encourages compliance with key NIST standards that they most likely already use.
Another example of how NIST 8170 can be pragmatically applied is found in item number 7, or “Report cybersecurity risks.” Organizations can incorporate this when considering their escalation channels for risk reporting and leverage it to improve their organization-wide communication.
In short, mapping controls to frameworks like NIST 8170 creates connections that boost executives' understanding in the purpose of a cyber framework within their infrastructure and subsequently, the competitive advantage it can generate.
The Future of Cybersecurity Frameworks
One goal of the CSF is to help organizations avoid falling into a false sense of security by strictly relying on checklists of security controls. However, this point often goes unnoticed because organizations must adhere to a rigid and complex regulatory landscape. Furthermore, many organizations are more interested in becoming certified compliant rather than improving their cyber risk management programs.
NIST 8170 asserts that improved security posture and compliance are not mutually exclusive. As Item 2 addresses how businesses can “Manage cybersecurity requirements,” while also improving their security. Consider this, there are overlapping requirements for organizations that need to comply with industry regulations like the Health Insurance Portability and Accountability Act (HIPAA) and Payment Card Industry Data Security Standard (PCI-DSS). This reconciliation can help companies maximize resources to improve risk management efficiency and operationalize cybersecurity activities specific to their organization's profile.
As security spending grows in response to the rising cyber risks, it will become increasingly important for organizations to identify and prioritize risks based on their individual profile so they can choose the most appropriate solutions and filter out inadequate technology. NIST 8170 provides organizations a means to objectively assess the cyber posture of potential vendors, resulting in a simpler process for comparing cybersecurity capabilities and ultimately, integrating organization wide security.
Silent Sector understands the number of industry regulations organizations face today and consequently the growing number of vendors and solutions. We help businesses see through the cyberspace noise and turn the mundane, yet critical process of compliance into a competitive advantage. Contact us today to hear how we can enable your organization to securely focus on innovation and mission objectives all while achieving industry compliance.
https://www.nitrd.gov/nitrdgroups/images/6/66/Cybersecurity_Framework_03222018.pdf


