Whether or not companies want to admit it, every company is in the cybersecurity industry. This even applies to organizations like manufacturing who are not historically associated with technology. Unfortunately, in the age of digital transformation, many companies believe that simply allocating a couple of bucks to purchase “state of the art” security tools is enough to fend off threat actors. In an analysis conducted by the well respected FireEye Mandiant Security Validation team, it was uncovered that 53% of successful intrusions remain undetected despite having several security products. The research indicates that the majority of organizations need an overhaul of their cybersecurity strategy. In a previous article, we examined how the saturated vendor market has encouraged organizations to hastily purchase tools without really considering their organization’s specific need and thus, giving them a false sense of security. However, this blog seeks to expose why high ticketed solutions are unable to effectively detect and prevent the growing number of cyber-attacks.
Tools that are not customized tend to be useless
FireEye’s research was based on attack simulations in enterprise production environments across 11 sectors and covered 123 security technologies. They concluded that the security tools are not optimized in many business infrastructures, nor are the resources available to execute the necessary modifications. The result of unchanged default configurations puts a gap in an organization’s defense strategy straight out of the gate. In addition, the lack of tailoring after deployment makes tools hardly, if at all useful. Security teams should avoid the tempting mindset of “protect and forget” or “patch and proceed” because strong security is not a single rigid decision but multiple agile ones.
Additionally, security alerts are unreliable when the additional time is not taken to fine-tune tools or follow up on their effectiveness. This can open a whole host of security concerns as false positives or false negatives can quickly erupt and generate unnecessary noise to parse through. It is also important for businesses to consider how this can make a cyber attacker’s mission a little easier through evading detection. Moreover, FireEye also determined that 54 percent of organization detection tactics failed to identify adversarial lateral movement. This is particularly intimidating, as it typically takes 100 days for a company to know they have been infiltrated. The wealth of information that can be gathered from pivoting across a network through the course of 100 days is concerningly grave. This period from when an attacker enters a network to when the security team detects it is critical to mitigating the severity and loss. It is also why it is pertinent organizations customize their tools to efficiently detect and track threat actor's movements.
In one example shared in FireEye’s report, a Fortune 500 insurance firm’s security tool was misconfigured and allowed over a third of malicious file transfer attempts. Every environment has different levels of what is classified as ostensibly normal or baseline activity. Moreover, once this baseline is established security professionals can adjust their threshold for alerts to identify anomalous behavior. In the case of the insurance company, the attempts that were not blocked did not even trigger an alert in the organization’s Security Information and Event Management (SIEM) platform. A SIEM is a platform that aggregates all of an organization's logs and can be utilized to provide real-time analysis and correlation of various logs. SIEMs are notorious for being overpriced, but consequently can be incredibly advantageous to an organization's detection capabilities. The insurance company could have reduced their losses had they created SIEM alerts for FTP access or set thresholds for detecting irregular file transfer. Obviously, no organization sets out to deploy a high-end SIEM and gain little benefits, but operating them requires highly specialized employees from an already small candidate pool. A SIEM, however, is not the answer to 100 percent network visibility, but is a complementary tool that can be used with automated security products to provide a powerful defense perimeter.
Tool Bloat
“Tool bloat” is a term used to describe the heavy investment and rapid adoption of as many security products as an organization's budget permits. This is also largely in response to their understanding that attackers are circumventing traditional security controls and refining their techniques to reach objectives. It is also important to note that in the world of vendor security companies, we can guarantee that some company out there has a product for any issues you can think of. These products range from advanced traffic analysis, deception technology, user behavior analytics, next-generation firewalls, intrusion detection systems, SIEMs, and identity management platforms.
One of the misconceptions that FireEye’s report exposed is that aimlessly purchasing tools is not the path to security. This is because the products purchased are not optimized for their environment, but also the tools unintentionally mimic each other in terms of functionality. Instead, organizations should take a multi-layered strategy of complementary controls that are designed for an organization’s specific needs. These controls must also factor in the people processes, and technologies an organization employs.
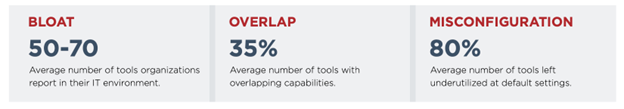
Image via FireEye
The reality is that there is no silver bullet or amount of money that can generate sound security. While on paper it seems an organization can become impenetrable through purchasing the right number of tools, this is simply not enough to achieve adequate security. FireEye’s report demonstrates that most organizations are not protected against cyber threats and their existing security infrastructure is not effective for accurately detecting attackers early on.
Contact Silent Sector today to learn how to validate the effectiveness of your cybersecurity strategy and ultimately ensure the resilience of your security program is adequate for the inevitable day your organization is targeted.


