A much-echoed rule in cybersecurity is that anything connected to the internet has the potential to be hacked. Despite office printers not looking like standard computers, they are no exception to this rule and still vulnerable to hacking. Last year a Russian hacker group infiltrated several organizations through unsecured printers. This resulted in silent spying and exfiltrating of company print jobs.
Why printers?
More often than not, office printers are seen as nothing more than a tool to produce hard copy documents. However, they are a treasure trove of sensitive and proprietary information because they are commonly relied on at all levels. Beyond the obvious threat of anyone being able to steal a classified document off a printer, printers often keep a record of printed documents in their memory. Additionally, printers are complex devices that rely on several different mechanisms to function. Mechanisms like networking protocols, printer languages/fonts, drivers, and connected apps all have vulnerabilities that predispose printers to becoming hacked. These vulnerabilities range from information disclosure to remote code execution. At DefCon 2019, one of the world’s most distinguished hacker conventions, 35 vulnerabilities in six commonly used enterprise printers were uncovered in a session titled “Why You Should Fear Your Mundane Office Equipment.”
It is easy to lose sight that printers are really just devices with embedded computers that use software to execute simple commands. However, embedded computers have been used to initiate numerous attacks such as the Target breach which occurred after malware was installed on a point of sale system. With printers being corporate wide relied on devices they also have a huge attack surface. This surface also makes it easier to attack printers because they commonly have web-based interfaces and wireless capabilities. Moreover, printers act as a point of entry for attackers to gain a foothold into a network because rarely are they segmented from workstations. Once a threat actor has gained access to the internal network they can run a simple network scan to look for other insecure devices and pivot until they gain access to high privileged accounts. Thus, achieve a hacker’s original objectives.
Printers can also be used to forward other attacks like Distributed Denial of Service which can overload websites and services with junk internet traffic. At a more rudimentary level, hacking a printer can also be used to crash the printer and potentially be catastrophic for standard business operations. In industries such as healthcare and legal services, functioning printers are mandatory for supporting mission objectives.
How do they hack?
Printers are often compromised through open security ports on an office network. These open ports can be scanned to detect the device, operating system, and much more. Services like Shodan, enable hackers to scan the internet for network connected devices and then find devices to target.
Traditional barriers in hacking printers like geographic location are eliminated with Shodan because an adversary’s reconnaissance phase is streamlined. The reconnaissance phase is fundamental to a successful attack and Shodan only makes it simpler to identify potential targets. Discovering open ports of internet connected devices is simple for anyone with access to a computer. Moreover, from the cybercriminal perspective, the number of victims can significantly increase, scaling up their chance of successfully reaching objectives.
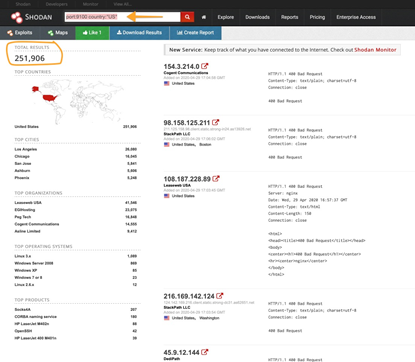

We used Shodan to scan for IoT devices with port 9100 (a commonly used port that printer manufacturers use for raw TCP data) globally and within the US – Results reveal top OS, vendor products, and organizations with this port open
What do printer hackers want?
The answer varies widely depending on the threat actor, but the majority of cyberattacks are designed to gain unauthorized access to data that can later be exploited. In other cases, hackers try to make money by holding data ransom. The motives behind the printer attackers are unclear but researchers believe they might be trying to spy on companies through their vulnerable printers.
It is important to consider that printers rarely have protections like antivirus, threat detection, or “no execute bits” which create a basic level of security for desktops and mobile devices. These are important for detecting malicious software or indicators of compromise on an endpoint. In which case, evidence of a printer attack includes the installation of a computer script. This script evades detection and can then be used for persistence on a network, giving attackers long term access to a victim’s network. Furthermore, since most organizations do not monitor the logs from their printers, they make excellent backdoors for access into a network.
What can you do to reduce the probability of a printer hack?
Taking advantage of weak printer management is how attackers are infiltrating organizations. Fortunately, there are several actions organizations can take to protect their printers and protect their business security.
- Change default administrator username and password
- Never keep the default values, especially when a new device is connected to the network
- Regular firmware updates and close monitoring for update releases
- losing printing access for a few minutes is a small fee to pay when the alternative could be a devastating cyberattack
- Disable any printer settings that involve printing over the Internet
- Network printers can be hacked using the method described above, so it is better simply to disconnect your printer from the Internet, in which case it will still be accessible through the local network
- IP Filtering
- specifies particular devices permitted to connect to the printer by registering their IP addresses to the printer
- matches a filter rule to data traffic based on any combination of IP source or destination address, protocol, source or destination port, the direction of flow, or time
- Security as a marketing advantage
- Considering the security implications on printers reduces an organizations vulnerabilities - enhancing their overall security posture and attentiveness to customer needs
For organizations and small businesses, it is certainly important to apply the tip above, but a third-party company could be the most effective solution is ensuring your printer’s security features or lack thereof are operating as they should to avoid a cyberattack.
Call Silent Sector today to hear how we can guide you through the process of adding adequate security to your network connected devices like printers, ultimately giving you and your customers peace of mind.


